Hey there, fellow digital detectives! Today, we’re about to embark on a thrilling OSINT adventure, courtesy of TryHackMe – Sakura room. In this exciting challenge, we’re going to put our Open-Source Intelligence skills to the test. But fear not, this room is designed to be beginner-friendly, so if you’re new to OSINT, you’re in the right place!
Imagine being in the shoes of a cyber-sleuth, armed with nothing but your wits and an internet connection. Our mission? To catch a cyber-criminal by uncovering hidden clues and digital breadcrumbs scattered across the web. It’s like being part of a virtual detective agency, and you’re the star investigator!
So lets start with the case details presented to us and unravel the truth.
Background
The OSINT Dojo recently found themselves the victim of a cyber attack. It seems that there is no major damage, and there does not appear to be any other significant indicators of compromise on any of our systems. However during forensic analysis our admins found an image left behind by the cyber-criminals. Perhaps it contains some clues that could allow us to determine who the attackers were?We’ve copied the image left by the attacker, you can view it in your browser here.
Task-2 Tip Off
The image itself doesn’t really give much info to us but we can surely find some relevant info about it in its metadata. In order to extract and gather all the required metadata we’ll use a CLI tool called exiftool.
Metadata from Exiftool :-
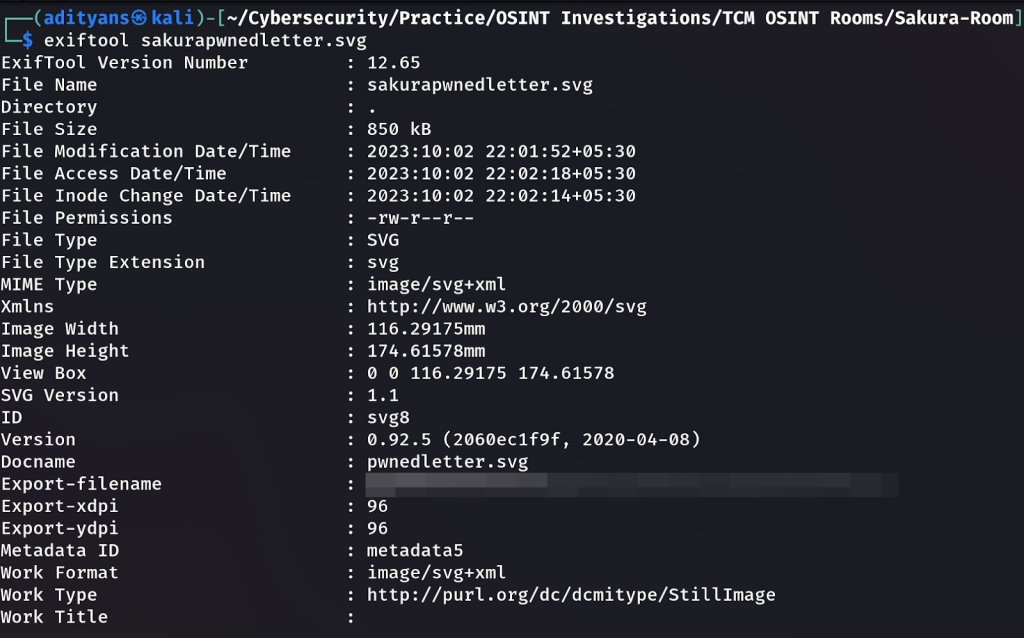
We can see that in the field name Export-filename, value reveals the username which is the answer to our first question..
Now onto the next task…..
TASK – 3 : Reconnaissance
Background
It appears that our attacker made a fatal mistake in their operational security. They seem to have reused their username across other social media platforms as well. This should make it far easier for us to gather additional information on them by locating their other social media accounts.
Now because social media sites were mentioned and we already had a username, I thought why not let’s take some help from Sherlock.
This is the result that I received from Sherlock and to say the least I was expecting something more, anyway I started to check out each of those profiles and nothing really caught my eye.
Although I stumbled upon this Github profile and thought this might be it but then left the site thinking it might just be a random user with low activity.
Then I thought of manually searching through websites and seeing if I can find anything with some variation of that same username, but to no avail.
I came back to read the instructions again and noticed that there is somewhat stress given on looking for the username in a job hunting website, so I quickly started looking for the username in popular sites like Linkedin, Glassdoor etc.
After getting nowhere eventually I needed a bit of help & guidance so I took reference of this writeup posted by Chad Warner and after going through the 2nd answer, it clicked me and now I knew exactly what I had to do.
So I went on to visit that same github profile again and the user has created 3 repositories named : PGP, IO and ETH. In the PGP repository we can see there is a file called publickey which contains PGP Public Key. Took that public key and pasted it onto CyberChef for Base64 decryption and guess what, we were able to locate the email address of this user.
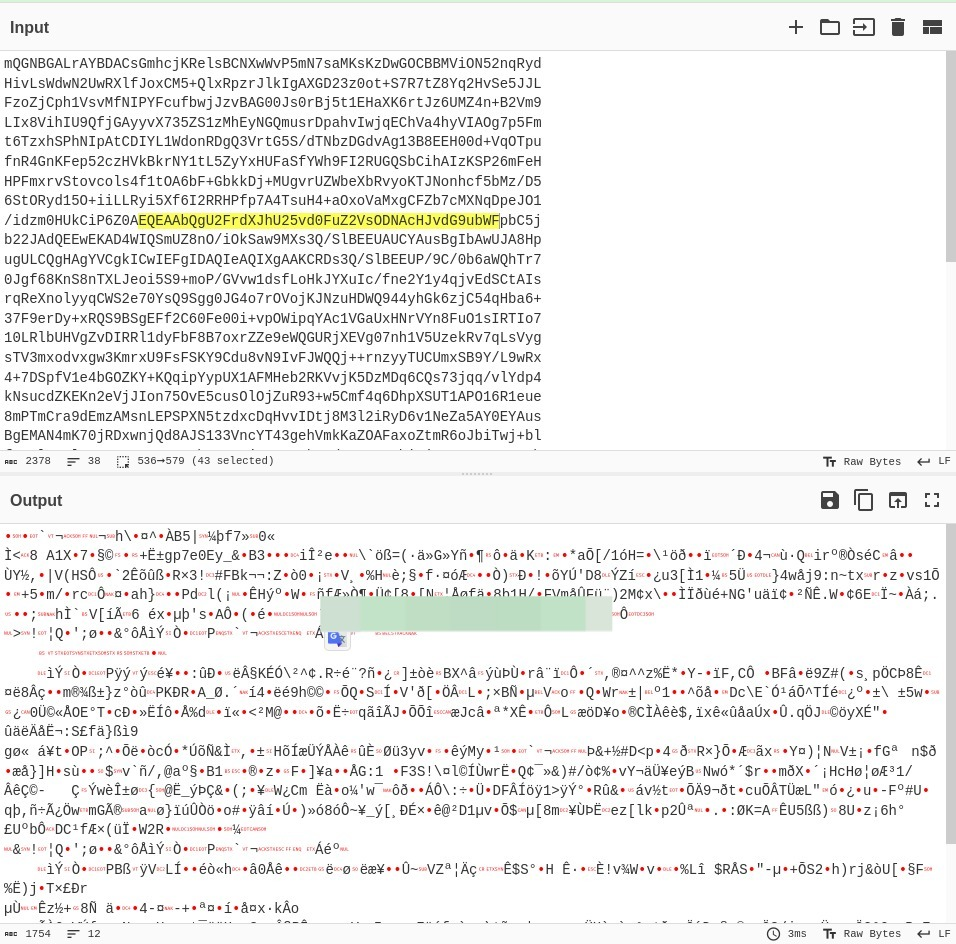
Which brings us to our 2nd answer for this room.
Next we need to find the Full Name of this person, and as of now we have the username and the associated email address for this. It occurred to me that I can get some info about them from one of the job hunting websites, so now I started curating search results with google dorking to specifically target those sites.
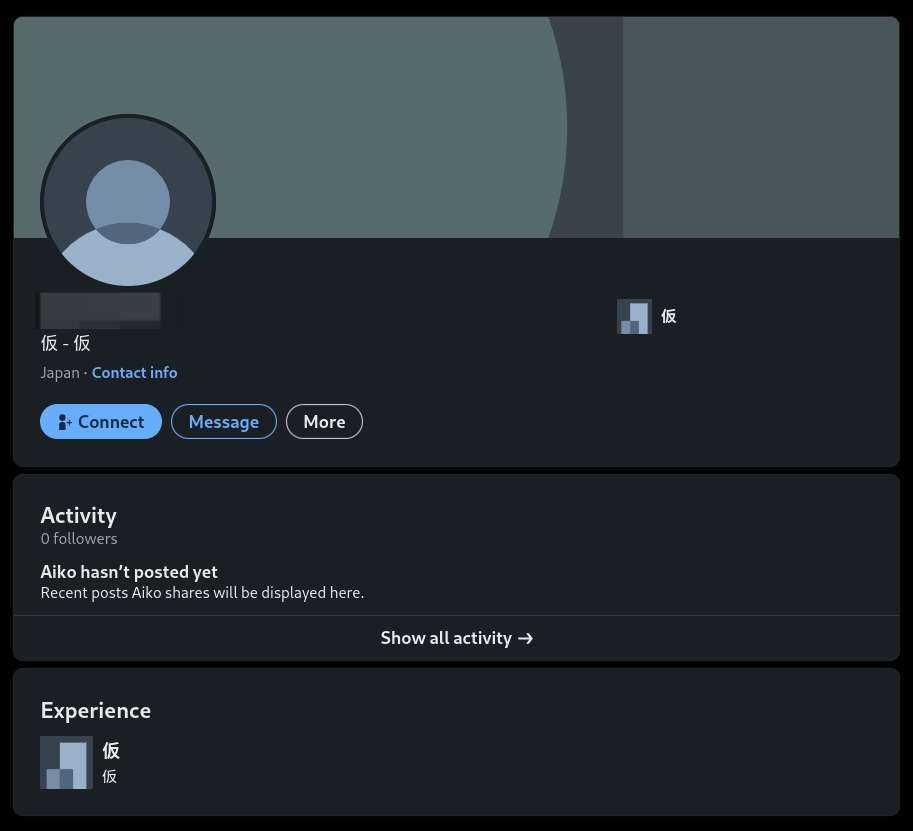
I got nothing other than the below posted result which at first also didn’t seem much lucrative, anyhow I went on to check these accounts and almost all of them were pretty normal and nothing seemed to be suspicious or odd in any way.
Except for one of them which was really weird because that profile had no posts, connections, followers, following or any other generic information. This was the one that stood out among others and I tried the name of this person on TryHackMe’s answer field, which to my surprise was the correct answer.
So finally we have our third answer for the question Full Name.
TASK – 4 : Unveil
Background
It seems the cybercriminal is aware that we are onto them. As we were investigating their Github account we observed indicators that the account owner had already begun editing and deleting information in order to throw us off their trail. It is likely that they were removing this information because it contained some sort of data that would add to our investigation. Perhaps there is a way to retrieve the original information that they provided?
Reading all the instructions I instantly knew that we are going to find some relevant info in the git commit of that github user account. Now upon visiting that account again the only cryptocurrency that the user owns is ETH – Ethereum which is also our answer for this task.
Although this – stratum://ethwallet.workerid:password@miningpool:port is the content you will find upon visiting this miningscript file, it is not the correct wallet address.
For that we need to look into the history of this account and as you can see that there are 2 commits performed over this file, upon checking them we can confirm it.
Now lets see what exactly were the changes that were made, which may eventually lead us to the next step.
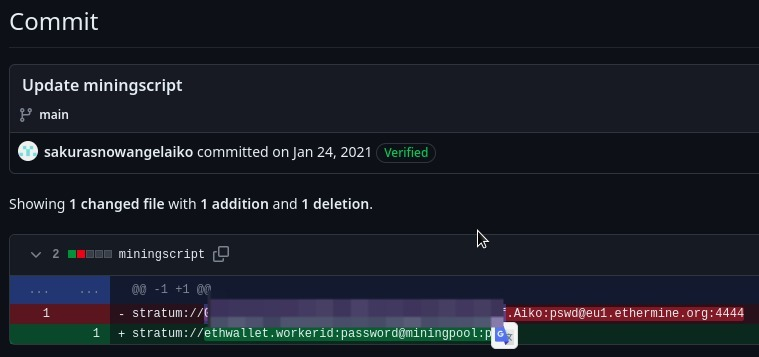
Ahhaaa…..gold mine!!! We got it, as you can see now that earlier this file miningscript used to contain not only the crypto wallet address but also user id, password and port details also. So we eventually got our answer for this question.
For the next part of the task we are supposed to figure out the mining pool that the attacker received payment from at a specific date. Now to be very fair I am no crypto genius, but to my part all I can do is a simple search so I began with all that I have i.e. attacker’s crypto wallet’s address.
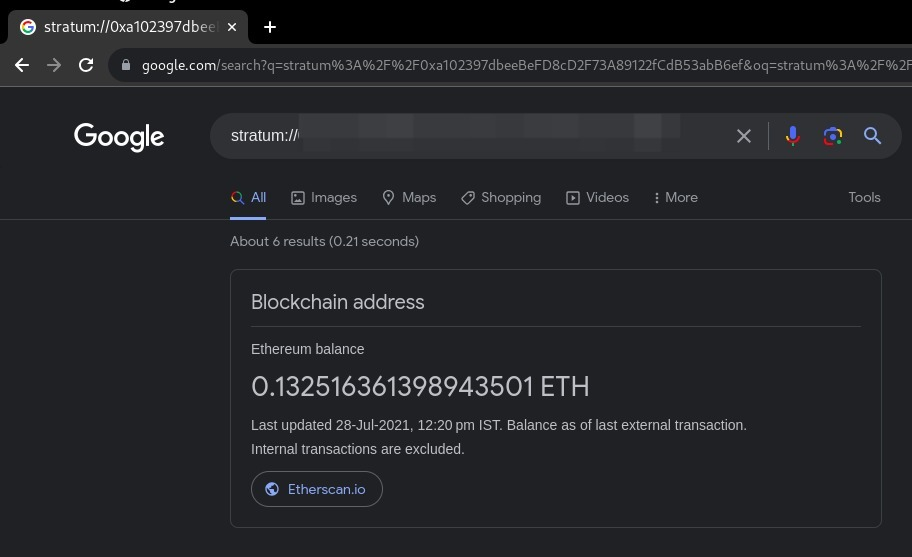
Doing so I got some results about this particular wallet and maybe this site can give me more information, so I visited it and provided the wallet address. Surprisingly it presented me with all the transactions that took place associated with that crypto account.
Now my task was to find the transaction that took place on January 23, 2021 UTC, and the 6th transaction from bottom matches our requirement.
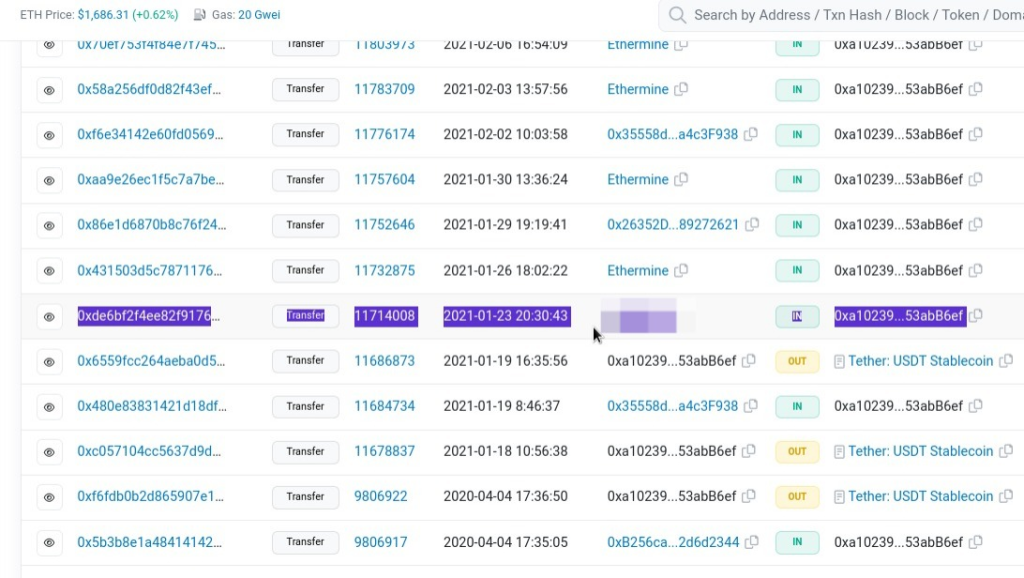
This is the exact transaction that took place and the relevant details associated.
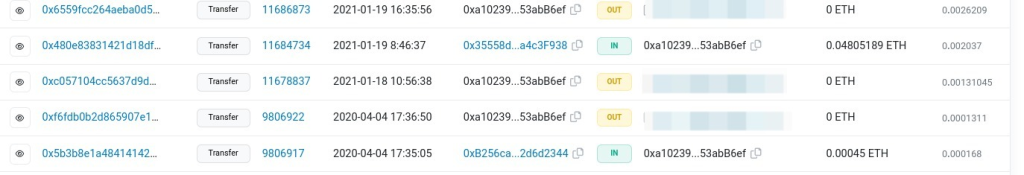
Now for the next answer we just needed to look for the transaction that doesn’t contain ETH and we found the answer.
TASK – 5 : Taunt
Background
Just as we thought, the cybercriminal is fully aware that we are gathering information about them after their attack. They were even so brazen as to message the OSINT Dojo on Twitter and taunt us for our efforts. The Twitter account which they used appears to use a different username than what we were previously tracking, maybe there is some additional information we can locate to get an idea of where they are heading to next?
We’ve taken a screenshot of the message sent to us by the attacker, you can view it in your browser here.
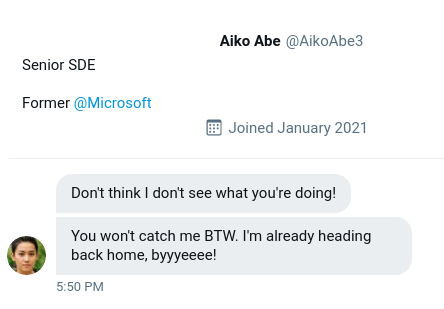
This is the screenshot provided to us that is said to be a conversation between OSINT Dojo and the attacker on Twitter, but this time they used a different account. Let’s first find this one and then go through the tweets to gather more info and make sense of it.
The next question requires us to figure out the URL where the attacker has posted their Wifi SSIDs and Passwords.
More context for this can be found in one of the threads posted by the attacker on twitter.
In the 2nd tweet there is a clever hint hidden, which tells us the exact location where the SSIDs and passwords might have been pasted, which is DeepPaste.
And just to make it clear I wasn’t actually able to crack this, instead I had to take hint from TryHackMe (although I knew it had something to do with those capitalized words)
This is the image we get when we visit the link provided to us in the hint.
And now we need to add b2b37b3c106eb3f86e2340a3050968e2 in the url of this page to make it complete and we can finally submit it as our answer.
In the next task we are supposed to find the BSSID for the attacker’s Home Wifi.
The SSID and password are already listed in the above image, so I just need to find a way to associate these details to their BSSID.
Went on to Google to find something and came across this site called wigle.net which seemed extremely old and I tried to work around it but didn’t get the result.
Then after trying my hands on multiple things I came back to the hint provided and it said that we might need to login and perform an advanced search.
So I went back to that same site, logged in and clicked on the advanced search option.
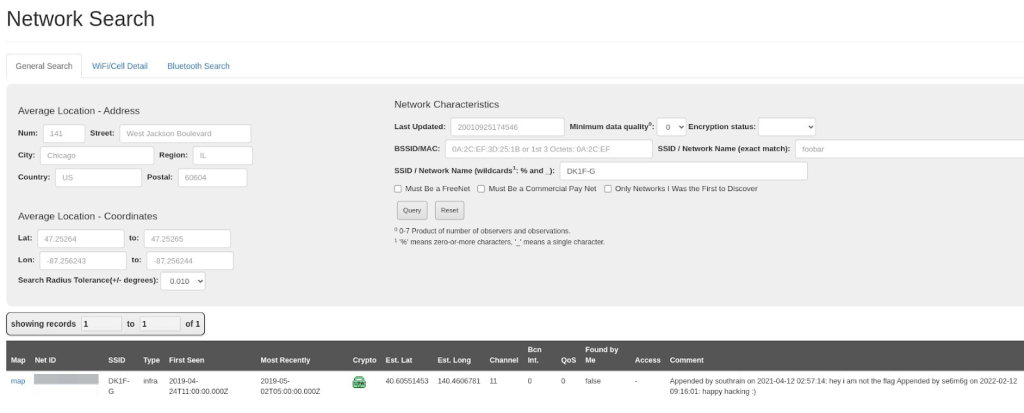
After putting in DK1F-G as the SSID, it gave me the BSSID associated with it.
Although I wasn’t sure if this is the correct one or not, I tried it anyway and got through it.
TASK – 6 : Homebound
Background
Based on their tweets, it appears our cybercriminal is indeed heading home as they claimed. Their Twitter account seems to have plenty of photos which should allow us to piece together their route back home. If we follow the trail of breadcrumbs they left behind, we should be able to track their movements from one location to the next back all the way to their final destination. Once we can identify their final stops, we can identify which law enforcement organisation we should forward our findings to.
First of all we need to find the place that the attacker was at before leaving for their home through aeroplane.
One of the tweets that the attacker made can give us a hint.
The tweet confirms that the attacker was at this place moments before leaving for the airport, so we need to find this place first.
Upon performing a reverse image on this we came to the conclusion that this place is Washington Memorial and the nearest airport from here has to be Ronald Reagan Washington National Airport.
Now as per the criteria we need to provide the airport code which is ***
Moving on to the next task where we need to find the airport which was the last layover for them and to do so we have yet another tweet which gives away a bit of info.
The sign reads JAL First Class Lounge Sakura Lounge and upon searching a bit I stumbled upon this site that has the complete list of all the International Airport Lounges associated with Japan Airlines.
I checked each of them one after another and the correct one is https://www.jal.co.jp/jp/en/inter/service/lounge/hnd/first/ as they have the 5 star rating
The airport code for this is ***
For the next task I needed help from google maps to figure out the location of the image.
This was the tweet that mentioned that the land visible in the image is quite close to the attacker’s home, upon putting it through google reverse image, one of the results caught my eye as they had the same geographical boundaries.
The result suggested that it is somewhere near Chubu, Japan, so I went on to google maps in order to search for this place but the actual location that is shown in this image was far from Chubu.
Now we can look for the lake names which can be determined if we filter out the geographical map data for lakes and it will eventually reveal the anwer.
For the next and last answer, we need to go back to the SSID and Password screenshot that we received, one of the entries mentioned City Free Wifi and its value is HIROSAKI_FREE_Wi-fi. The value gives away the city name and upon checking, it aligns with the route of the previous image where we discovered the lake.
And there you have it, our whirlwind adventure through the “Sakura” room on TryHackMe. We’ve peeled back the digital layers, followed clues, and honed our OSINT skills together. It’s been a journey, hasn’t it?
Remember, OSINT is like a never-ending puzzle; there’s always something new to discover. So, keep exploring, keep learning, and keep that cyber-sleuth spirit alive. Thanks for joining me on this quest, and until next time, happy hacking and stay curious!


Well done!!
Thank you buddy
( ˶ˆᗜˆ˵ )